3.5 Entaglement base to protocol
The protocol using entanglement are called
entanglement-based protocols, Ekert protocols or EPR protocols. This
protocols was discovered by Arthur Ekert at 1991. EPR protocols use
pairs of photons which are entangled. The pairs photons entangled can be
produced by both Alice and Bob or other person. The main idea for E91, is to
use three possible states and testing no violability of Bell inequality that to
detect the evesdropper in the channel. The entanglement protocol follows three
steps:
1. The imposibility for Alice to preduct which polarization she
will get as a result;
2.
Section 3.6. Attacks on a QKD channel Page 19
Secondly, If Alice and Bob carry out polarization of measurement
they will not have a perfect correlated answers but same will be correlated;
3. Last is the Eavesdropper will be detect for every tentative
by Bob and Alice.
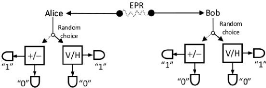
Figure 3.6: QKD entanglement protocol
We may need to mention that as quantum cryptography is dueling
with light (photon), the transmission of informations between terminals using
QKD for security implies appropriate devices for connexion. So, the
transmission in this field is done by a channel call quantum channel
and is composed by optical fiber. When Arthur Ekert proposed the
protocol, he based the assumption that Alice and Bob can test the Bell's
inequality by verifying the entanglement of particle. This assumption allows
that the generation of is secure key still possible as long as the entanglement
is verified. This part have more explanation in [QQL10a]
3.6 Attacks on a QKD channel
Since we said that quantum cryptography have a sure security,
that did not avoid in mind of people to find a way to attack. In classical
cryptography, we can mention attacks like brute force, frequency there are many
attacks. Is still the same for quantum cryptography, people developed some
attacks concepts but till now quantum cryptography is still not crackable. Let
us list some attacks used.
1. Individual attack : This attack as you can guess by the
name, is an attack acting in each qubit in the channel. The systems for this
attack are prepared separately (independantly). An example for this attack is
an intercept - resend;
2. The collective attacks : The difference from the first one
is to perform Eavesdropper result. That will joint a measurement to get more
information
3. Coherent attack : This attack one of the powerfull attack
that Eve can use because it has all possible things that she can do. Here, she
has to do an albitrairy preparation of joint state (entanglement) where the
interaction of each qubit must be before the measure being joint in the
channel.
The figures below will describe a little bit the explanation of
each attack for QKD.
Section 3.6. Attacks on a QKD channel
Page 20
Eve individuel Mea urerneal
Bob
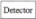
A1iaa
Ere AeciI
Figure 3.7: Indivivual Attack
Light Moe
·
Alice
Source
Eve Cal led we Measuremeal
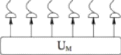
Big Aael1lie
J
Figure 3.9: Cohence attack
Figure 3.8: Collectif attack
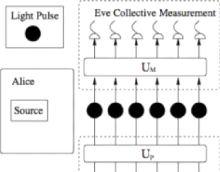
Light Plc
·
Eve Collective Mesiuirrrnc ll
ars'
Alice
Some
Bob
Manor
Eve Collrcti.ve Ancitie
21
| 


