3.3 Assumption and protocol
Untill now the research considered a QKD as the only one key
exchange which is secure. After their experience and verification, they came up
with same characteristics to show us that this system stayed a secure system
and the eternel system secure. Let us enumerate them.
1. This system give an guarantee to detect the Eve presence in
the channel;
2. The key is absolutely secure that does not depend to the
complexity of the algorithm or the technology used by Eavesdropper to
attack.
Having those assumptions with a properties of quantum
mechanics, quantum cryptography provide two kinds of protocols. All the
protocols are able to detect the Eavesdropper in the channel and have the
unconditional security.
3.4 Protocols Using Heisenberg's
There are many protocols using this notion of HUP but for us,
we will focus on those which are more used and discovered before. We may have
in mind that all the protocols follow the same structure6.
Prepare and send protocol
After Weisberg publish a paper where he introduced the concept
of quantum mechanics in communication, Bernett and Bassard in 1984 come up with
a new revolutionnary idea which was the first proposal of QKD protocol using
totaly HUP (based on quantum properties) notion. This protocol is the oldest
for quantum cryptography, based on basis7 which are quite related to
the polarization notion. We have the rectilinear and the diagonal basis for
BB84. Quantum protocol can be describe in two steps or phases, quantum and
classical one. Let us describe firstly quantum phase and classical phase
after.
Quantum phase
Any message passing through in the computer are converted into
zeroes and ones which are the informatic unity in classical information theory.
In BB84, there exist a correspondant unity for quantum information to express
information. Using Dirac notation, we express the information unity with a
braket as |øi, |1i or |xi and its call qubits 8.
Other definition, we call a qubit a superposition of zeroes and ones
(|00i, |01i, |10i) , is described by complex number with an
argument 1 belong the set
{á|0i + /3|1i : |á|2 + |/3|2
= 1;á,/3 ? C}, (3.4.1)
we take |0i and |1i as two references qubits, corresponding to
two orthogonal states in a quantum system.
6Structure means the fonctionnality is the same but
few differents we can find but in general is the same
7BB84 is the main protocol and the remaind follow
the way that its works the difference is few certain have a difference just in
basis used to send the information
8Quantum bits
Section 3.4. Protocols Using Heisenberg's Page 17
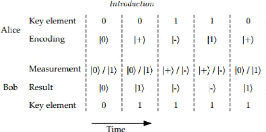
Figure 3.3: Transmission photon by Alice to Bob
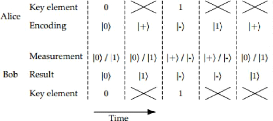
Figure 3.4: Detection of photon by Bob using states
measurement
1. In BB84, Alice sends a sequence of photon to Bob, each
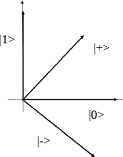
independantly choose one of the four polarization (the four polarization are
vertical, horizontal, 45% and 135% you can have an idea checking the figure
down).
2. For each polarization, Bob will choose one base for
measurement to achieve the result
3. Bob will records the result and his measurement bases and
after, he will publicly acknowledges his receipt other signal.
Classical phase
In this phase the entities have a following steps
1. Alice broadcasts her bases of measurement, Bob broadcasts his
bases of measurements
2. Alice and Bob discard all events where they use different
bases for a signal
3. To test for tempering, Alice randomly choose a fraction,
if all remaining events as test events, she publicly broadcasts their position
and polarization
4. Bob broadcasts the polarizations of the test events
Section 3.5. Entaglement base to protocol Page 18
Figure 3.5: Data transmit between two parties using basis
5. Alice and Bob compute the error rate of the test events.
If the compution of error rate is large than some prescribed threshold value,
say 11% they about otherwise, they proceed to the next step (This step is where
Alice and Bob detect Eve presence)
6. Alice and Bob each convert the polarization data of all
remaining data into a binary string called a raw key. They can perform
classical post-procesing such as error correction and privacy amplification to
generate a final key.
With quantum mechanics properties, the security is a
efficiency and the Eavesdropper can use any method of attack Alice and Bob will
detect her. The work of [Zha09] explain other notion for the efficiency
security.
3.4.1 B92 protocol . This protocol is a
derivative of BB84 protocol. It was proposed by Charles Bernett in
1992. B92 have the same function then BB84 but the difference is just the half
part of fonctionality from BB84. The encoding of one state for example
|ø) composed by {|0), |1)} we can encode each element of the set in this
way the first element in the set will be encode with rectilinear basis which is
correspond to 0o and |1) encode in diagonal basis this according to
[Hai14]. There exist also other variants QKD protocols using the notion of
Heisenber Uncertainty Principale as you can see in many book where they are
talking about QKD like [Hai14]. We can enumerate other protocols using
Heisenberg like, Six-State Protoco(SSP) proposed by Posquinucci,
Gusin in 1999 the different with BB84 instand of two state and here the
use one.
| 


