5.1 Network
We know that to share information between two entities, we
need connexion and for that, there existe same models which were build by
people and published after second world war by ARPA-NET project. That project
was a PETENGONE project in second world war it was impossible for them
to share or contact other bases for sharing data so the upcome of network idea.
A network by definition is a group of two or more computers (Equipments)
systems linked together..
A network follow a model and that model allows an implication
of several steps which are called layers. Let us talk little bit about
the composition of layer.
5.1.1 Model. In network, there exist two
kinds of models that according to the convention of IEEE1,
The OSI and TCP/IP model. The OSI model is composed by seven layers
and TCP/IP is composed with four layers. For our part QKD, we will be more
interest in OSI model and try to explain how the QKD was implemented in the OSI
model and how its works in this model also were precisely researchers
implemented in classical model to become a quantum model. You can see in the
figures how the models look like.

Figure 5.1: Network Model
5.1.2 Integration of QKD in the OSI model layers.
In the begining of 21st century, people used the genius
idea to implement a QKD in the OSI model and this implementation was focus in
some types of layers. The layers where QKD was implemented are session layer,
network layer and the data link loyer. Those layers seem are more important.
The combination of QKD with other protocols in OSI model, is
for an efficiency related to quantum field.
1IEEE (Institute of Electrical and Electronics
Engineers) is a organisation where all networks conventions are approved
Section 5.1. Network Page 26
Section 5.1. Network Page 27
We have a combination with a TLS/SSL in the session layer, in
the network layer where more result are related to the connexion, the QKD find
a cohabitation with an IPSEC protocol, the combination gives a new kind of
protocol called SEQKEIP and the last layer, we have a Q3P is
the mixage of QKD with PPP protocol.
Implementing a QKD in OSI model, give an explanation that the
QKD network technology might be an essential part of modern security schemes
for high performance distributed computing application. This implementation of
secure scheme in OSI model was a project funded F6 called SECOQC which
is a global network and the meaning is given by Secure Communication based
on Quantum Cryptography. This project was developped by BBN
technology, DARPA, researchers of Harvard University, Boston University in
2014. The combination give us the sophisticated protocol and QKD network
architecture.
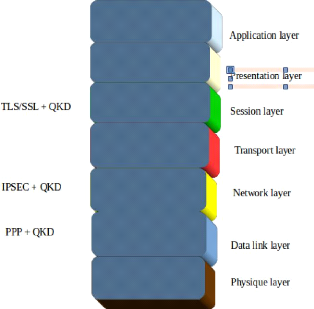
Figure 5.2: QKD implementation in OSI model
There exist a system which coordonate various network tools
such that standard, open, general proposed protocols all those compose a system
architecture and the system is called a grid. Grid computing is
emerging as a modern technology to fulfill the high performance. Computing
requirement of users, institutions and business organization world wide that
was clear in [KX]
5.1.3 Functionality. In this point, we used a
paper of [EAA]. The example take, is the integration of QKD in TLS/SSL for
secure a transaction. That is related with online-commerce and palpaye
classically, we have a secure server and protocol Htpps, the connection use
TLS/SSL mode.
/This protocol ensure a integrity of the message and the
encryption using point-to-point connection
between client and server. The combination of TLS/SSL with QKD
is called QSSL and can be described as two principal modes. The first
modes is about authentification of two sides which are communicating, that
communication is in QKD.
The client and server after authentification, the following
main operation continue to complete the generation of key size negociation and
in the end of the operation of generating key size, the change-cipher-spec and
finished messages can be exchanged.
The second method called the handshaking this method
is a pre-shared keys initialization based on the previous model-1, the
transactions (messages) are inserted before the transmission of
change-cipher-spec and finished message.
The protocol QSSL has been added in the SSL record protocol.
For this quantum cryptography with a principal toll QKD, can be integrated
within SSL/TLS. In SSL, we have an additional parameter which is the Alert
Protocol. Let us describe the fields than the messages follow in quantum
cryptography and the fields can be represented in table where we will
summarise
1. Describe the message use in public exchange phase of the QKD
protocol with a type of 2 bytes
2. Specification of QKD protocol used type 1 bytes
3. Allows the use of more than one version of certain QKD
protocol version 1 byte
4. length (4 bytes) the length of the messages is in bytes.
5. Jo. no 2 bytes QSSL session all operation multiple QKD
protocol instance belong on it.
6. Authentification 1 bytes : specification of the message
whether is authentificated. The idea of this point was taken in the article
[EAA]
|
Type
|
Protocol
|
Version
|
|
Length
|
|
|
Job no
|
Authentication
|
Encoding
|
|
Content
|
|
|
Tag
|
|
/The integration of QKD in network layers. The network layer
is important because in this layer, when we want to ensure a point-to-point
connection between two distinct people and to determine a data travel, the
layer has a capacity to find the short way and quick one using some parameters
for the reach the destinator. There are the most important job for this layer
in OSI model and for the communication. The OSI model use what we call
IPSEC2 with a comming of QKD in 2003, BBN
technologies found a way to integrate a QKD with the IPSEC protocol and
that combination give the another current protocol named
SEQKEIP3.
The new protocol which act with a main toll of quantum
cryptography, has one idea in this construction and the idea is to stick, to
traditional IPSEC and ISAKMP4. Those protocols, you can have some
deep information like how its works in web site of RFC 2409, this is what we
called norm RFC. QKD with
2Internet Protocol security
3Secure Quantum Key Exchange Internet Protocol
4Internet Security Association and Key Management
Protocol
Section 5.1. Network Page 28
IPSEC gives a SEQKEIP, to build simply, we have to define two
phases of Internet Key Exchange and that its the same as the use of ISAKMP
mechanics, that takes an advantage to QKD in order to build a pratical
protocol.
SEQKEIP have three mains in functionnality or phases: phase 1
is the negociation of the ISAKMP SA, phase 2 is negociation of SA and the last
is phase 0, in this Alice and Bob will share the first secret key as adding in
the phase. SEQKEIP have three modes, Quantum mode, Main mode, Quick
mode. All those modes correspond to the phases listed in top. Quantum mode
include quantum cryptography with a key exchange in phase 0, during the
negociation phase of IASKMP SA, we can assimilate this phase to main mode and
when we have the negociation of SA, the corresponding relation in SEQKEIP is
the quick mode.
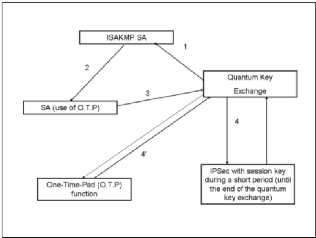
We can now explain how SEQKEIP works. We will see in the next
figure, the action are numerated.
1. The fixation parameters of our protocol, that will be done
with ISAKAMP SA and SA in other way is the combination of main mode and quick
mode.
2. The implication of QKD using key Exchange with or either
one-time-pad function
3. In last part, is the use of traductional symmetric
cryptography algorithms for exchange of data.
We must put in mind that this operation, the lifetime of
session key is so very short. Its equal to the time need to exchange the secret
key using quantum cryptography. Whitout QKD, IPSEC work in the same manner. The
idea of the quantum cryptography is to sift completely to the unconditional
security function (QKD and OTP). You can find many explanation on [STH]
/Integration of QKD in data link : The data link provide the
physical address service to the upper layer and is the only one add a queue to
ensure the validation of data. This layer provide physical adress
Figure 5.3: SEQKEIP functionality
Section 5.1. Network Page 29
which is MAC address to the equipment. In classical part of
network, the protocol used in this layer is PPP5 adding in this a
quantum notion, we will leave a classical communication and will reach quantum
networking. The combiation of PPP with QKD that provide a new protocol call
Q3P.
The integratin of QKD in data link, provide some steps to
achieve the right information. The steps that we list in this part we get
inspiration in the writing of [EAA]. Let us illustrate brievely which steps for
Q3P :
1. In this first step, we have an action of dead, establish,
authentification. The three actions are identical to PPP, that mean the first
phase pass through 3. The negociation of Encryption start just after the
authentification operation for two nodes and the parameters are negociated
also
2. The second phase is if the encryption key functions
successfull, the requirement, the QKD phase will directly start. The encryption
negociation is along the Key length and the TTL6 by sending a proper
ECP7 packet
3. The quantum cryptography exchange will start directly with
one goal to share a secret key in both nodes, that the goal of QKD. The
encryption algorithm will be shared and the TTL of the key. The key that we get
will be used in the network phase.
4. The data are sending through the channel, it is enciphered
using the key production in the previous step and the algorithm also.
The following enumerate all the steps of Q3P. As we said that the
TTL is short so far that when the
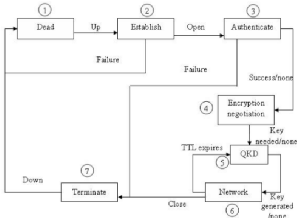
Figure 5.4: Q3P
TTL is expired, a new QKD phase start automatically. You can
see in the picture how can we be build a network with the same equipment and
include a QKD implementation in that network.
5PPP: Point-to-Point Protocol 6TTL: Time to
life
7Ecryption Control Protocol
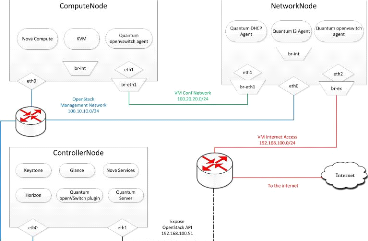
Section 5.2. Databases future work Page 30
Figure 5.5: Quantum network Architecture
| 


